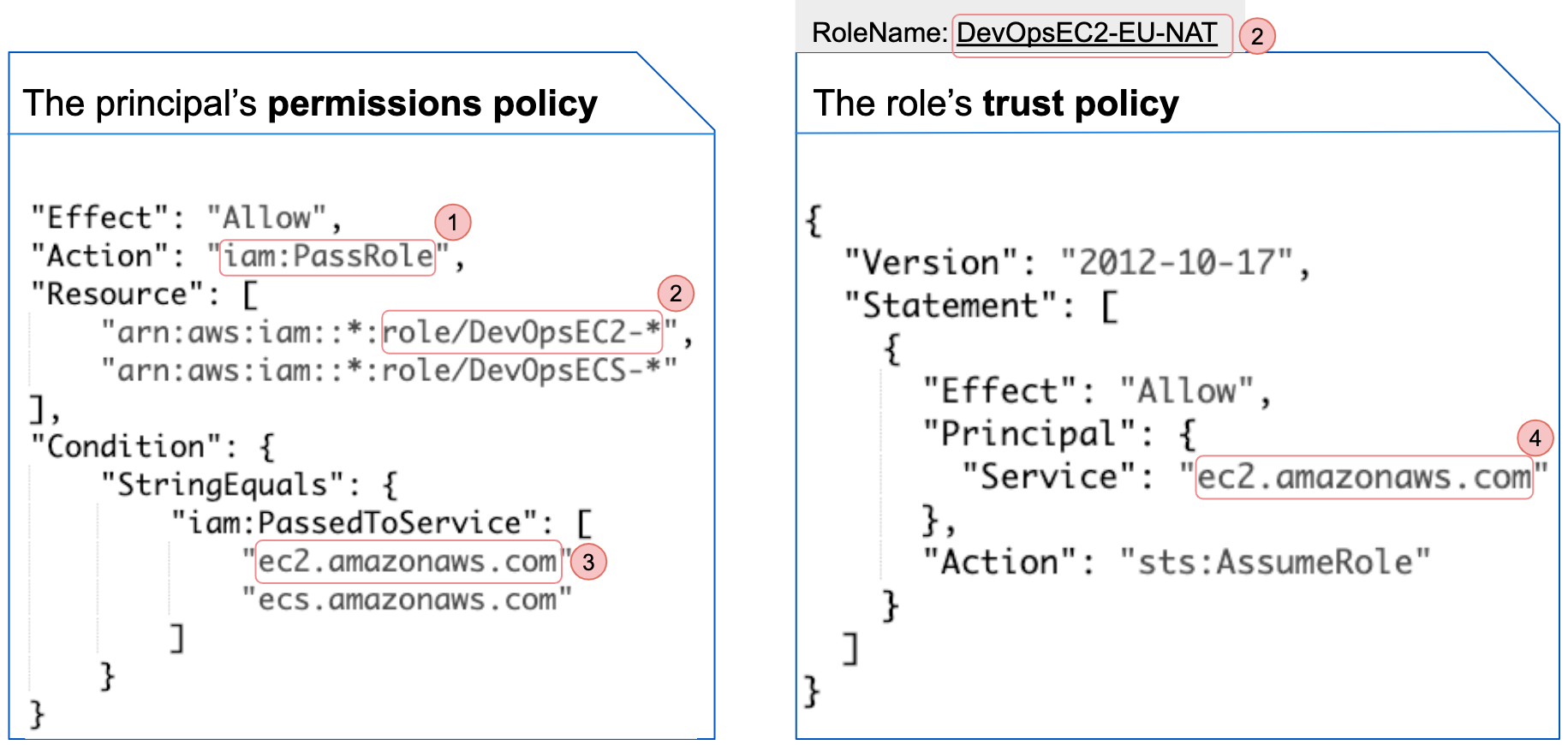
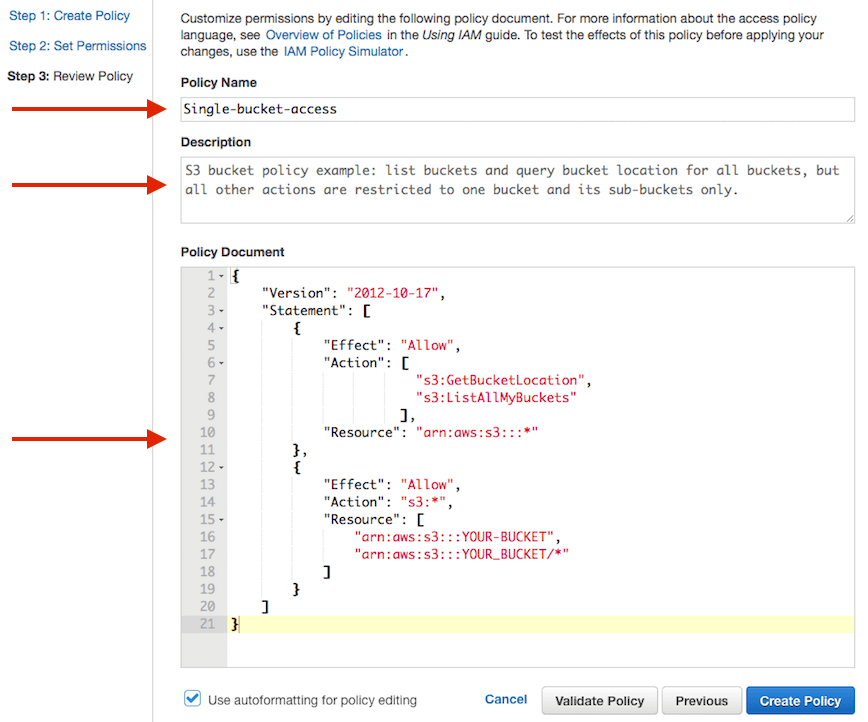
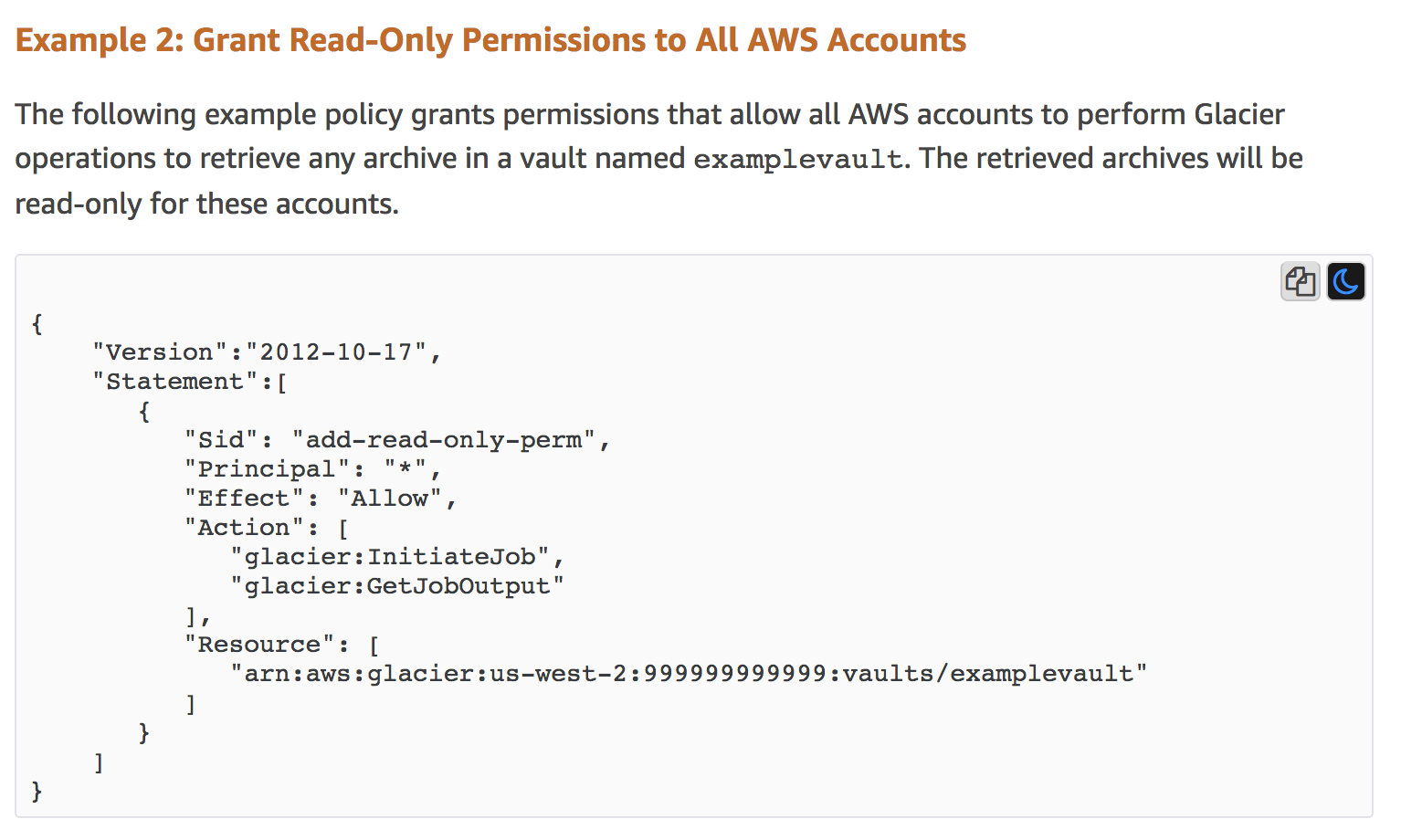
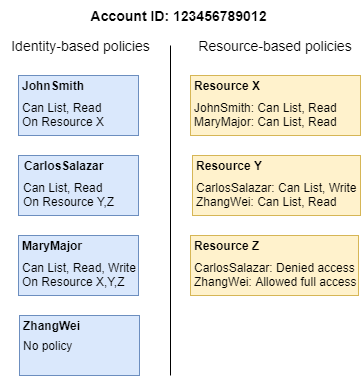
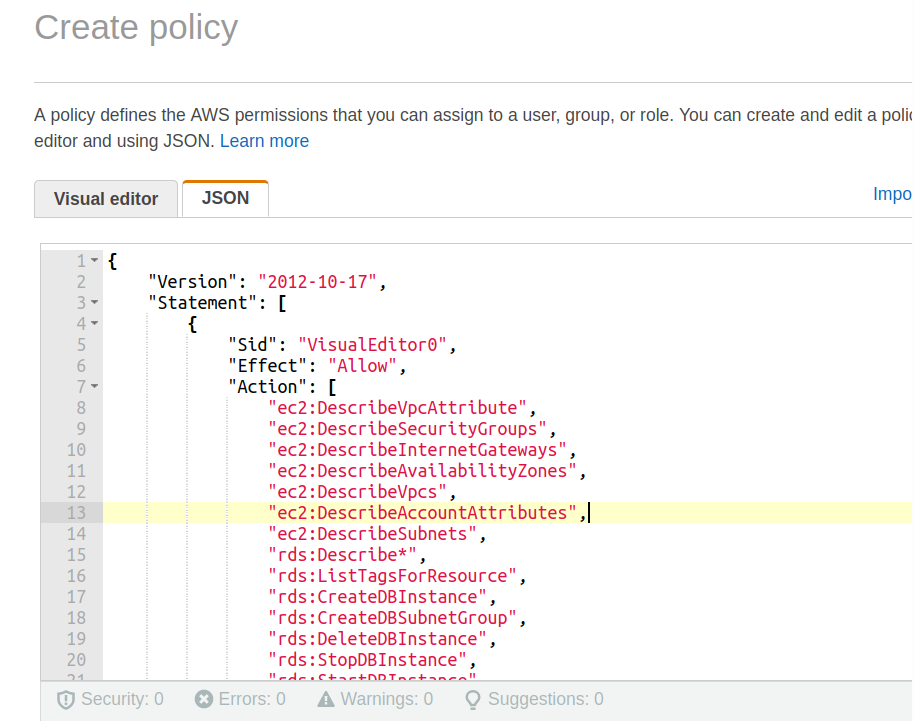
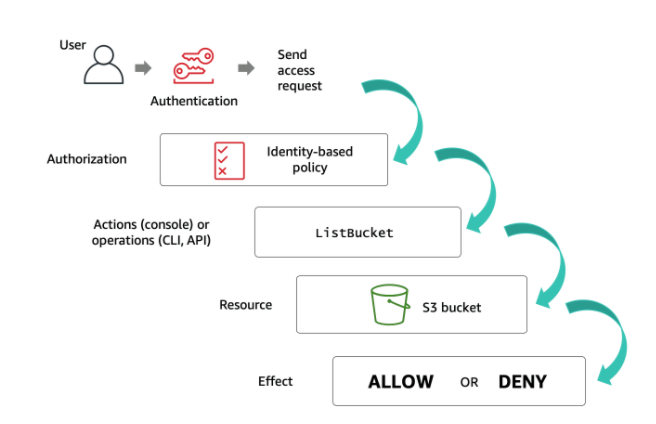
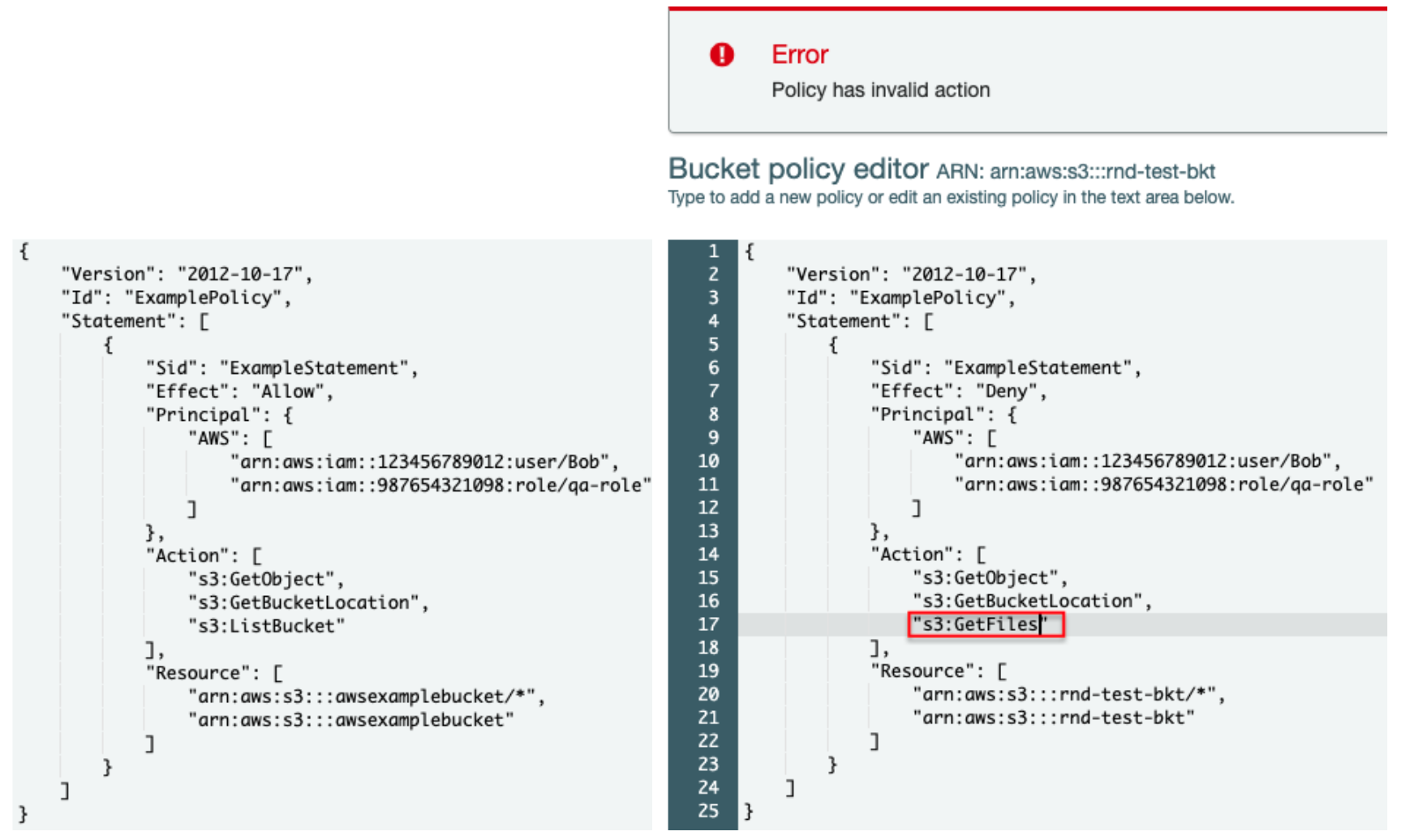
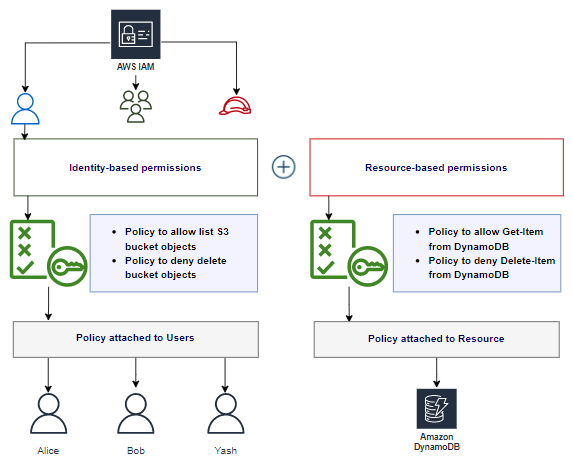
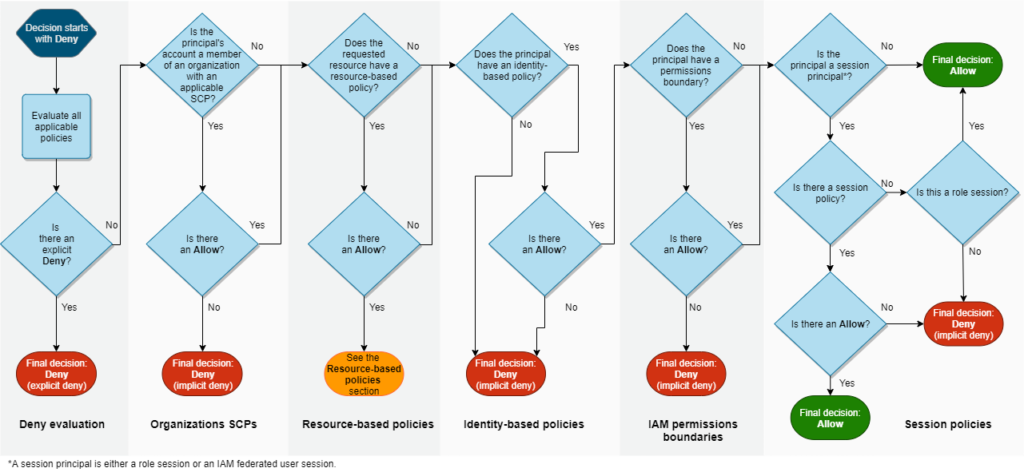
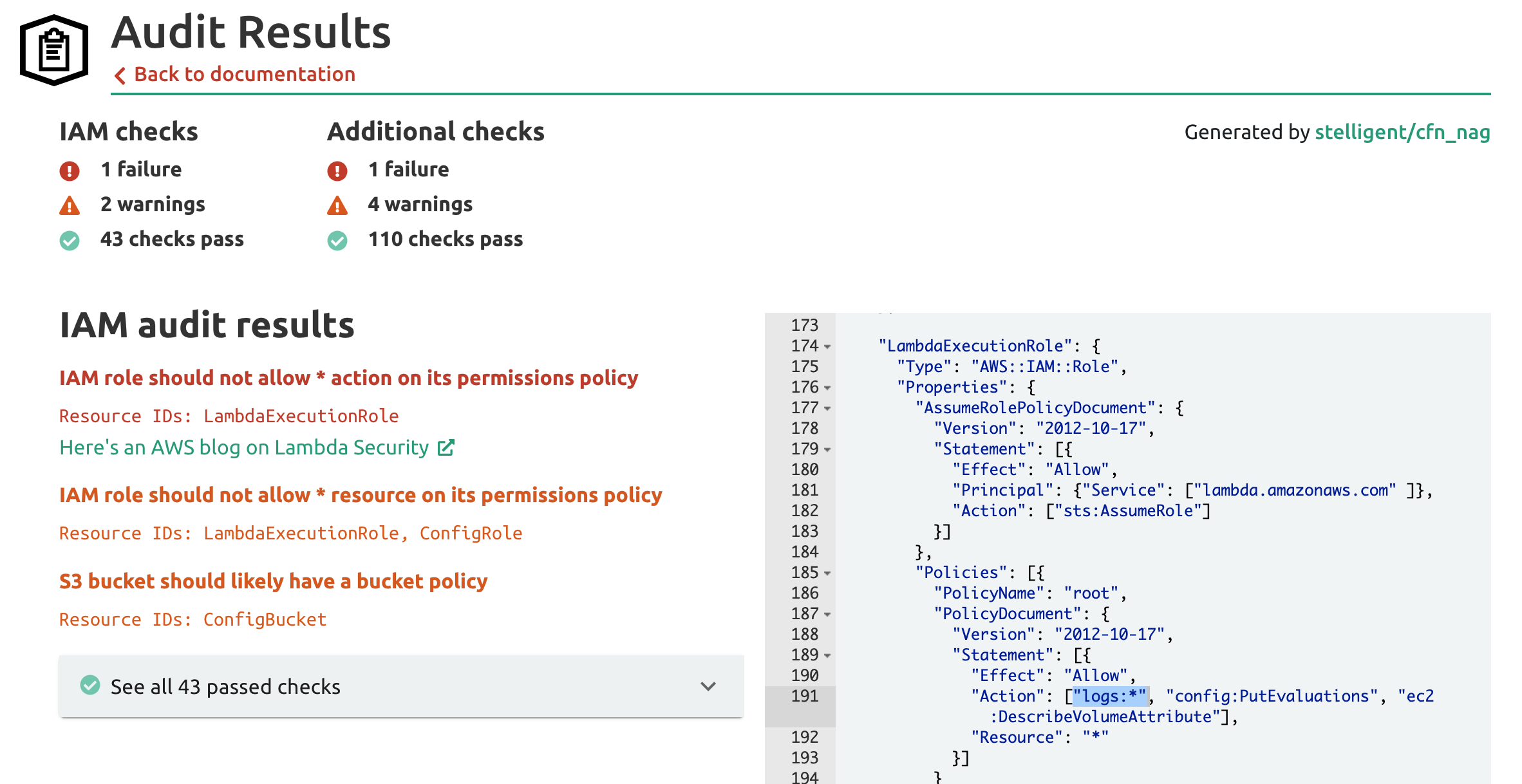
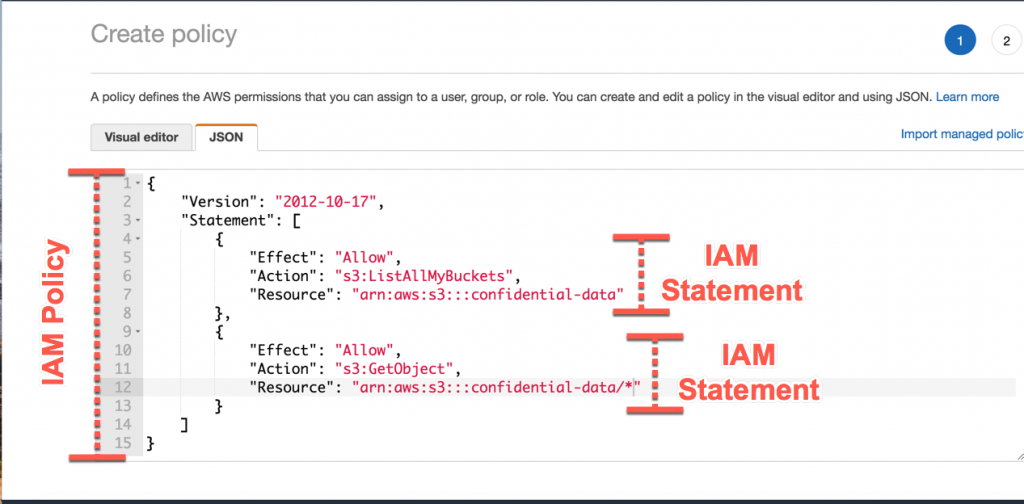
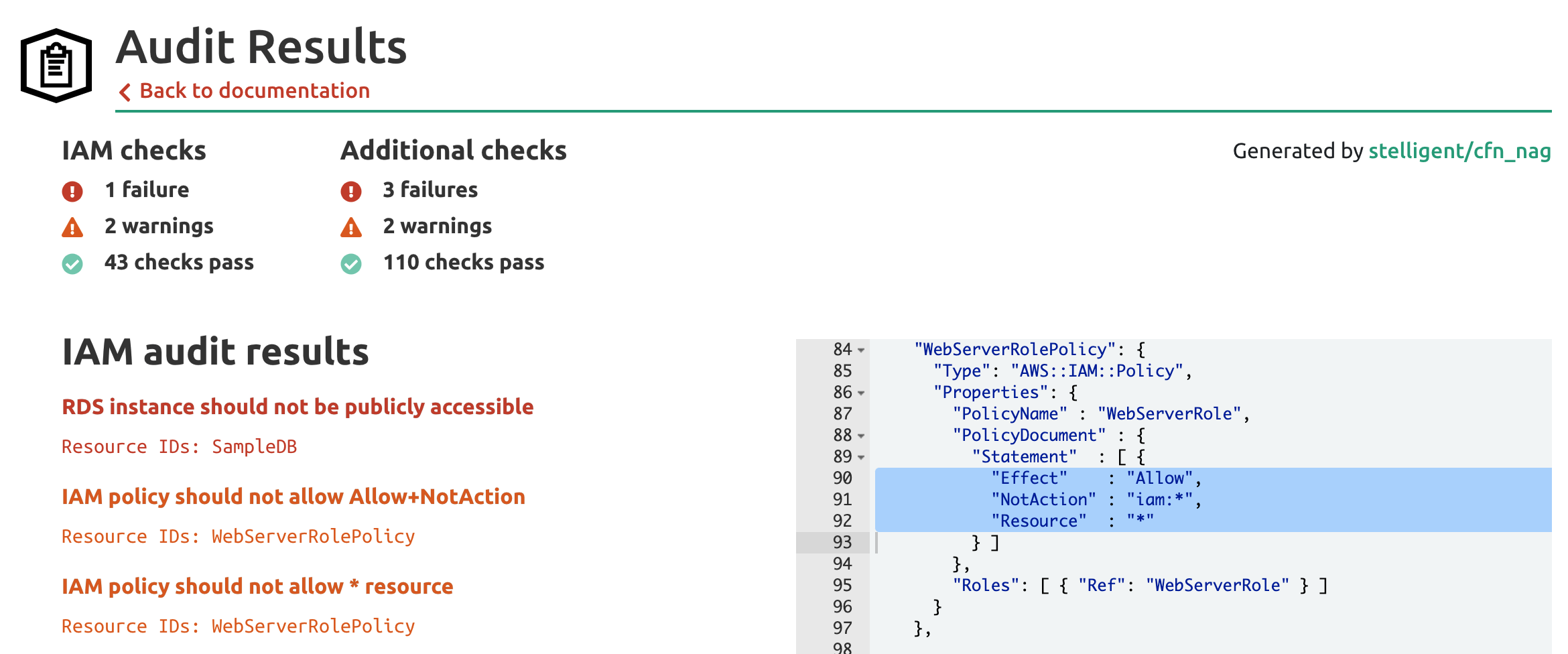
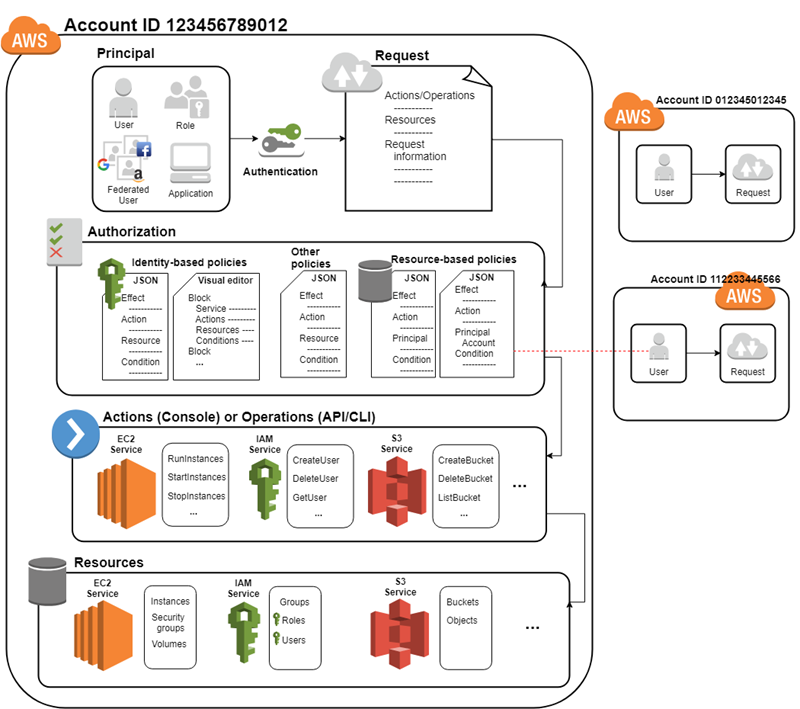
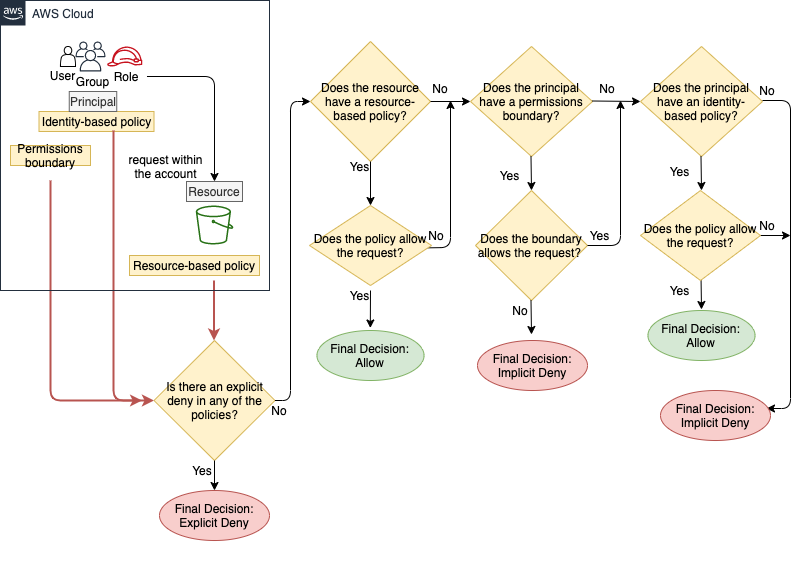
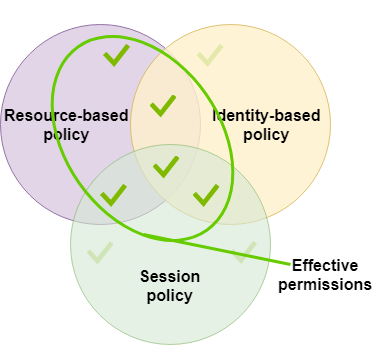
AWS Security on Twitter: "👀Learn when you should use the following AWS IAM policy types, and who should own and manage the policy: ➤Service control policies ➤Permissions boundaries ➤Identity-based policies ➤Resource-based policies

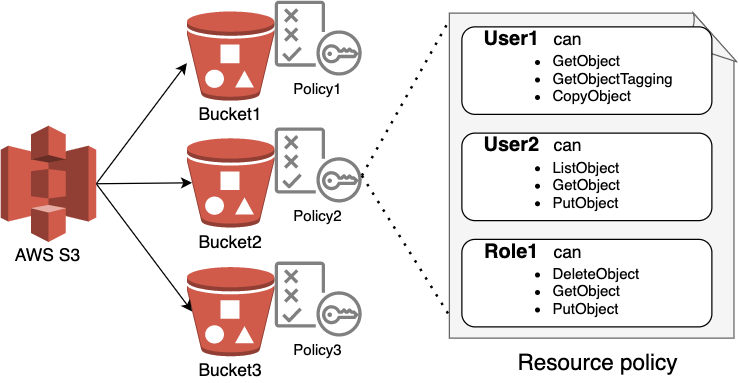
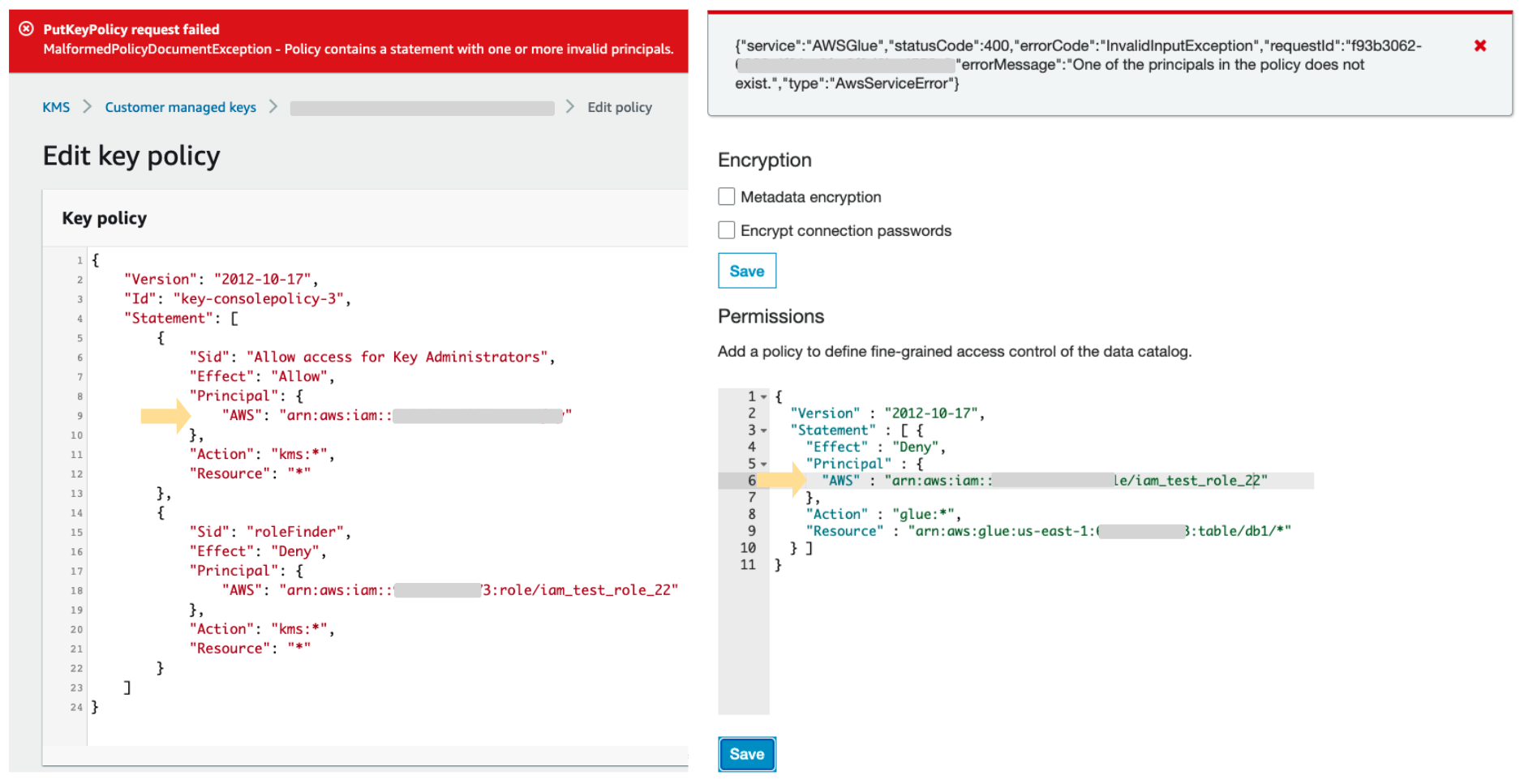
How to use resource-based policies in the AWS Secrets Manager console to securely access secrets across AWS accounts | AWS Security Blog
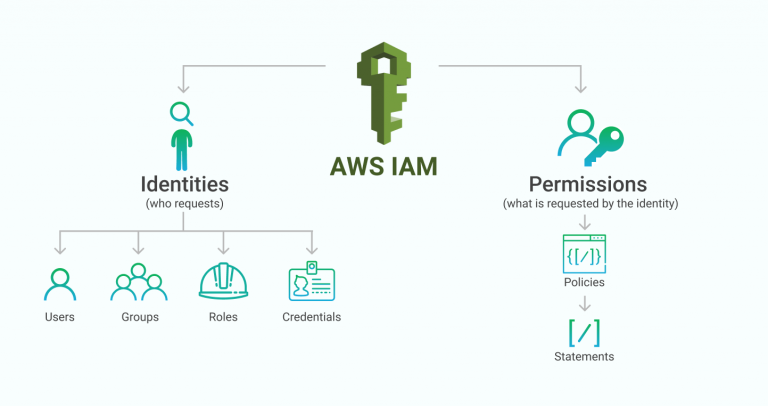
AWS IAM Primer. The 20% of IAM that you need 80% of the… | by George Lutz | Trimble MAPS Engineering Blog | Medium